How to Make Fake Login Page to Hack Someone
Introduction
In today’s digital age, cybersecurity has become a crucial concern. While it’s essential to protect our personal information online, it’s equally important to understand the methods that hackers employ to compromise our accounts. One such method is creating a fake login page to deceive unsuspecting individuals and gain unauthorized access to their accounts. This guide aims to shed light on the process of making a fake login page to hack someone, in order to increase awareness and enable individuals to better protect themselves.
1. Understanding the Concept of Fake Login Pages
Before diving into the process of creating a fake login page, it’s crucial to understand what it entails. A fake login page is a replica of a legitimate login page designed to deceive users into entering their login credentials, which are then captured by the hacker. This method, also known as phishing, can be highly effective if executed properly.
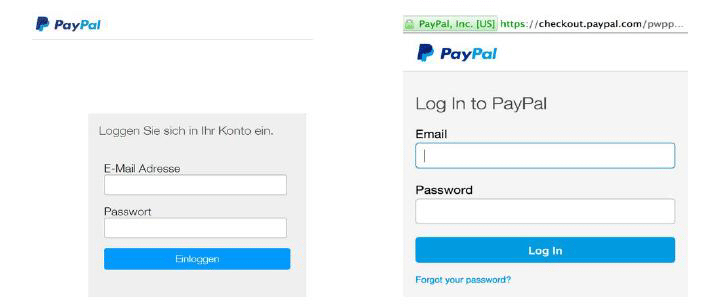
Steps to make your own phishing page:
2. Gathering Necessary Tools and Resources
To create a fake login page, you’ll need a few essential tools and resources. These include:
2.1. Web Hosting and Domain
To host your fake login page, you’ll need a web hosting service and a domain name. Numerous web hosting providers offer affordable plans suitable for this purpose. Additionally, you can register a domain name that closely resembles the legitimate website you’re targeting.
2.2. HTML and CSS
Basic knowledge of HTML (Hypertext Markup Language) and CSS (Cascading Style Sheets) is essential for creating a convincing fake login page. HTML allows you to structure the page elements, while CSS helps you style and customize the page’s appearance.
3. Crafting the Fake Login Page
Now that you have the necessary tools and resources, let’s delve into the process of crafting a fake login page.
3.1. Analyzing the Legitimate Login Page
To create an authentic-looking fake login page, you’ll need to closely examine the design and structure of the legitimate login page. Pay attention to the layout, color scheme, fonts, and overall aesthetic. This will help you replicate the page more convincingly.
3.2. Creating the HTML Structure
Using your knowledge of HTML, start by creating the basic structure of the fake login page. Begin with the <!DOCTYPE html> declaration, followed by the <html>, <head>, and <body> tags. Within the body section, you’ll add the necessary form elements to capture the user’s login credentials.
3.3. Styling the Page with CSS
Once you’ve created the HTML structure, it’s time to style the page using CSS. Match the fonts, colors, and overall design of the legitimate login page as closely as possible. This will enhance the authenticity of your fake login pages and increase the chances of fooling the target.
4. Implementing the Capture Mechanism
Creating a visually convincing fake login pages is only part of the process. To successfully hack someone’s account, you need to capture the login credentials entered by the target user. There are several methods to achieve this:
4.1. Client-Side Scripting
Client-side scripting languages like JavaScript can be utilized to capture the entered credentials as soon as the user submits the form. By attaching an event listener to the submit button, you can intercept the data and store it for later use.
4.2. Server-Side Scripting
Alternatively, you can employ server-side scripting languages like PHP to handle the form submission. The entered credentials can be processed on the server, logged, or sent to the attacker via email.
5. Spreading the Fake Login Page
To maximize the chances of success, it’s crucial to spread the fake login pages effectively. Here are a few methods hackers commonly employ:
5.1. Social Engineering
Social engineering techniques involve manipulating individuals into taking certain actions or divulging sensitive information. Hackers may use various tactics, such as sending personalized emails, creating enticing advertisements, or leveraging social media platforms to trick users into visiting the fake login pages.
5.2. URL Manipulation
Another method involves manipulating URLs to redirect users to the fake login page. This can be achieved through techniques like URL shortening or embedding the URL within enticing messages.
Conclusion
Understanding the process of creating a fake login page to hack someone is crucial for individuals to protect themselves from falling victim to such attacks. By being aware of the techniques employed by hackers, recognizing suspicious login pages, and practicing good cybersecurity habits, we can collectively enhance our online safety.
Henceforth, WE WISH TO ANNOUNCE THAT OUR SERVICES ARE NOT AVAILABLE TO PEOPLE FROM NIGERIA AND INDIA. THESE ARE USELESS TIME WASTERS AND THIEVES TRYING TO BEG OR SCAM US OF OUR PRODUCTS. OUR SERVICES ARE NOT FREE AND PAYMENT IS UPFRONT
A LOT OF FOOLS FROM NIGERIA AND INDIA. on the off chance that YOU DON’T TRUST TO USE OUR SERVICES, DON’T CONTACT US AS WE HAVE NO FREE SERVICE
CONTACT US FOR PURCHASES/INQUIRIES, WE RESPOND ALMOST INSTANTLY
HI BUYERS, WE ARE A PROFESSIONAL CARDING AND HACKING TEAM. HOVATOOLS HAS BEEN AROUND SINCE THE TIME OF EVO MARKET, ALPHABAY, WALLSTREET MARKET AND MORE. WE REMAIN STRONG AND RELIABLE IN THE INDUSTRY, ALWAYS PROVIDING YOU WITH THE BEST QUALITY TOOLS TO HELP YOU MAKE MONEY AND MAXIMIZE PROFIT IN THE FRAUD GAME.
TO GET STARTED, YOU CAN VISIT OUR ONLINE SHOP/STORE TO BUY EVERYTHING YOU NEED TO START CASHING OUT. AT THE SHOP YOU GET Accounts & Bank Drops CVV & CARDS DUMPS PERSONAL INFORMATION & SCAN.
BANK HACKING SOFTWARE – WIRE/ACH DARKWEB MONEY TRANSFER HACKERS
Buy Fresh Credit Cards for Carding, BIN LIST Buy Bank Login, RDP, Buy Hacked Paypal accounts. Contact us to buy all tools and carding software. CLICK HERE TO VISIT OUR SHOP
Buy Socks 5, Email Leads, Buy Latest CC to Bitcoin Cashout Guide, Buy Hacked Zelle transfer , Western Union Money Transfer Hack, Buy Hacked Money Transfer service to your bank account.
Enroll for Paid private Carding Class.

![You are currently viewing [hot] – How to make fake login page to hack someone [works]](https://hovatools.com/wp-content/uploads/2022/02/hovatool-post-image-23.jpg)


